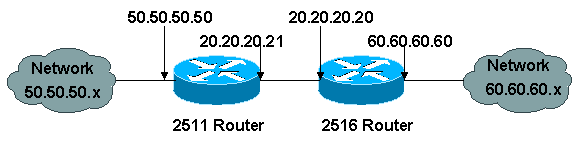
Cisco 2511 configuration
cl-2513-2A#write terminal
Building configuration...
Current configuration:
!
version 11.3
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname cl-2513-2A
!
!--- Override the default policy and use
!--- preshared keys for authentication.
crypto isakmp policy 1
authentication pre-share
group 2
!
!--- Define our secret shared key so
!--- you do not have to use RSA keys.
crypto isakmp key sharedkey address 20.20.20.20
!
!--- These are the authentication and encryption
!--- settings defined for "auth2",
!--- which is later applied to the crypto map.
crypto ipsec transform-set auth2 esp-des esp-sha-hmac
!
!--- The crypto map where you define your peer,
!--- transform auth2, and your access list.
crypto map test 10 ipsec-isakmp
set peer 20.20.20.20
set transform-set auth2
match address 133
!
interface Ethernet0
ip address 50.50.50.50 255.255.255.0
!
interface Serial0
ip address 20.20.20.21 255.255.255.0
no ip route-cache
no ip mroute-cache
!--- Nothing happens unless you apply
!--- the crypto map to an interface.
crypto map test
!
ip route 0.0.0.0 0.0.0.0 20.20.20.20
!
!--- This is the access list referenced
!--- in the crypto map; never use "any".
!--- You are encrypting traffic between
!--- the remote Ethernet LANs.
access-list 133 permit ip 50.50.50.0 0.0.0.255 60.60.60.0 0.0.0.255
!
line con 0
line aux 0
line vty 0 4
login
!
end
Cisco 2516 configuration
cl-2513-2B#show run
Building configuration...
Current configuration:
!
version 11.3
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname cl-2513-2B
!
ip subnet-zero
!
!--- Override the default policy and use
!--- preshared keys for authentication.
crypto isakmp policy 1
authentication pre-share
group 2
!--- Define the secret shared key so you
!--- do not have to use RSA keys.
crypto isakmp key sharedkey address 20.20.20.21
!--- These are the authentication and encryption
!--- settings defined for "auth2,"
!--- which is later applied to the crypto map.
crypto ipsec transform-set auth2 esp-des esp-sha-hmac
!--- The crypto map where you define the peer,
!--- transform auth2, and the access list.
crypto map test 10 ipsec-isakmp
set peer 20.20.20.21
set transform-set auth2
match address 144
!
interface Ethernet0
ip address 60.60.60.60 255.255.255.0
no ip directed-broadcast
!
!--- Nothing happens unless you apply
!--- the crypto map to an interface.
interface Serial0
ip address 20.20.20.20 255.255.255.0
no ip directed-broadcast
no ip route-cache
no ip mroute-cache
clockrate 800000
crypto map test
!
ip classless
ip route 0.0.0.0 0.0.0.0 20.20.20.21
!
!--- This is the access list referenced
!--- in the crypto map; never use "any".
!--- You are encrypting traffic between
!--- the remote Ethernet LANs.
access-list 144 permit ip 60.60.60.0 0.0.0.255 50.50.50.0 0.0.0.255
!
line con 0
transport input none
line aux 0
line vty 0 4
login
!
end
'IT 이야기' 카테고리의 다른 글
| DHCP공격에 대한 기본적인 Switch 설정 (0) | 2010.06.30 |
|---|---|
| Switch 기본 보안 설정 Root Guard & BPDU Guard (0) | 2010.06.30 |
| ESMTP에 대하여 (0) | 2010.06.17 |
| 642-832 tshoot .덤프 문제풀이 (0) | 2010.05.12 |
| 642-832 Tshoot 덤프 문제풀이 (0) | 2010.05.11 |
